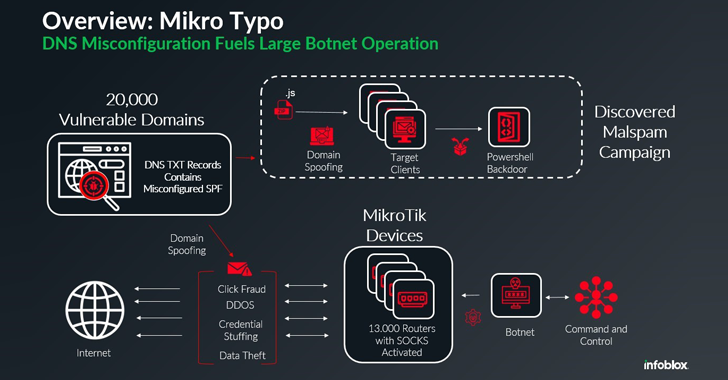
A global network of about 13,000 hijacked Mikrotik routers has been employed as a botnet to propagate malware via spam campaigns, the latest addition to a list of botnets powered by MikroTik devices.
The activity “take[s] advantage of misconfigured DNS records to pass email protection techniques,” Infoblox security researcher David Brunsdon said in a technical report published last week. “This botnet uses a global network of Mikrotik routers to send malicious emails that are designed to appear to come from legitimate domains.”
The DNS security company, which has codenamed the campaign Mikro Typo, said its analysis sprang forth from the discovery of a malspam campaign in late November 2024 that leveraged freight invoice-related lures to entice recipients into launching a ZIP archive payload.
The ZIP file contains an obfuscated JavaScript file, which is then responsible for running a PowerShell script designed to initiate an…