A new report from cybersecurity researchers at ESET has uncovered a massive botnet comprised of over 400,000 compromised Linux servers being used for cryptocurrency theft and other illicit financial gain.
The botnet, operated by the threat group behind the Ebury malware, has been active since at least 2009 but has evolved significantly over the past decade.
Ebury’s Insidious Spread
The Ebury gang employs a variety of techniques to propagate the malware and expand their botnet:
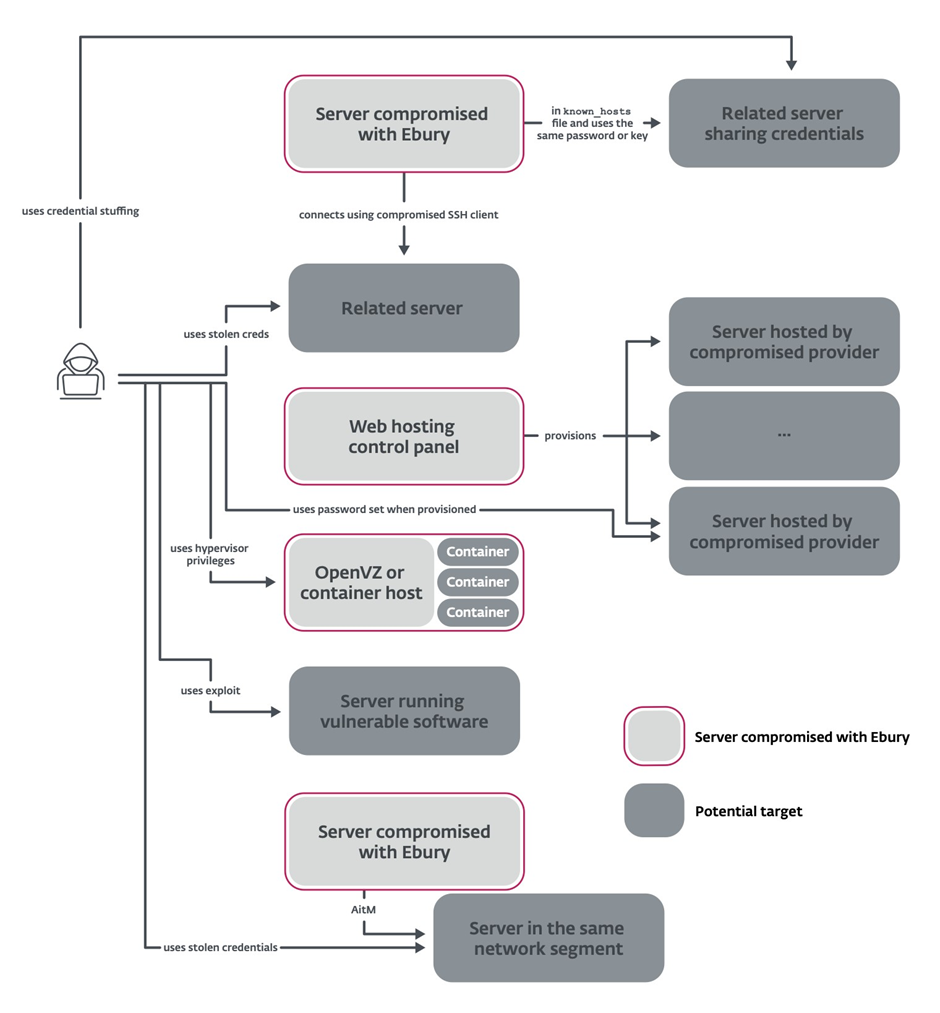
- Compromised Hosting Providers: Leveraging access to hosting companies’ infrastructure to install Ebury on all hosted servers
- ARP Spoofing Attacks: Intercepting and redirecting SSH traffic inside data centers to capture credentials
- Over 200 Bitcoin/Ethereum Nodes Targeted: Automatically stealing crypto wallets when victims log in
Free Webinar on Live API Attack Simulation: Book Your...