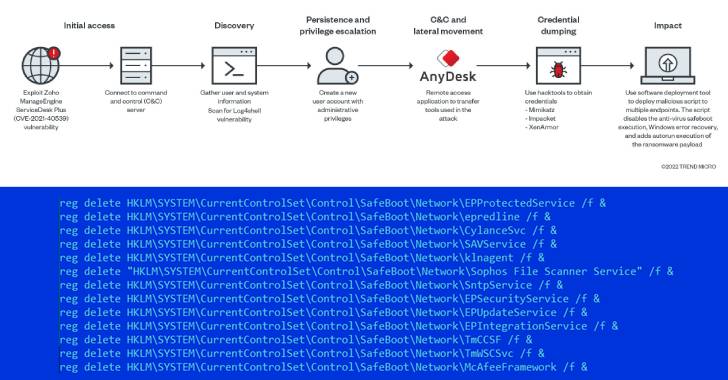
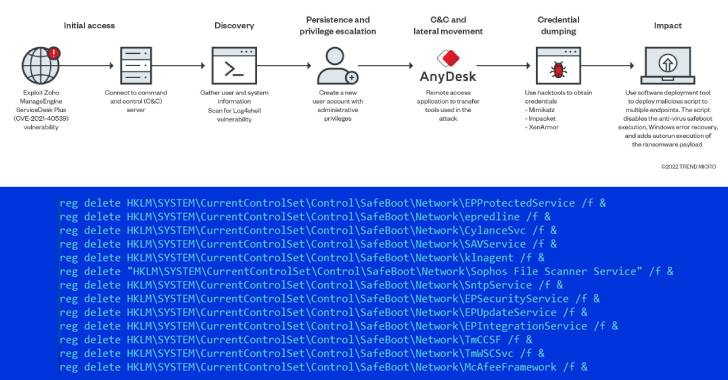
Cybersecurity researchers have disclosed a new variant of the AvosLocker ransomware that disables antivirus solutions to evade detection after breaching target networks by taking advantage of unpatched security flaws.
“This is the first sample we observed from the U.S. with the capability to disable a defense solution using a legitimate Avast Anti-Rootkit Driver file (asWarPot.sys),” Trend Micro researchers, Christoper Ordonez and Alvin Nieto, said in a Monday analysis.
“In addition, the ransomware is also capable of scanning multiple endpoints for the Log4j vulnerability (Log4shell) using Nmap NSE script.”
AvosLocker, one of the newer ransomware families to fill the vacuum left by REvil, has been linked to a number of attacks that targeted critical infrastructure in the U.S., including financial services and government facilities.
A ransomware-as-a-service (RaaS) affiliate-based group first spotted in July 2021, AvosLocker goes beyond double extortion by auctioning data stolen…