Targets located in Azerbaijan have been singled out as part of a new campaign that’s designed to deploy Rust-based malware on compromised systems.
Cybersecurity firm Deep Instinct is tracking the operation under the name Operation Rusty Flag. It has not been associated with any known threat actor or group.
“The operation has at least two different initial access vectors,” security researchers Simon Kenin, Ron Ben Yizhak, and Mark Vaitzman said in an analysis published last week. “One of the lures used in the operation is a modified document that was used by the Storm-0978 group. This could be a deliberate ‘false flag.'”

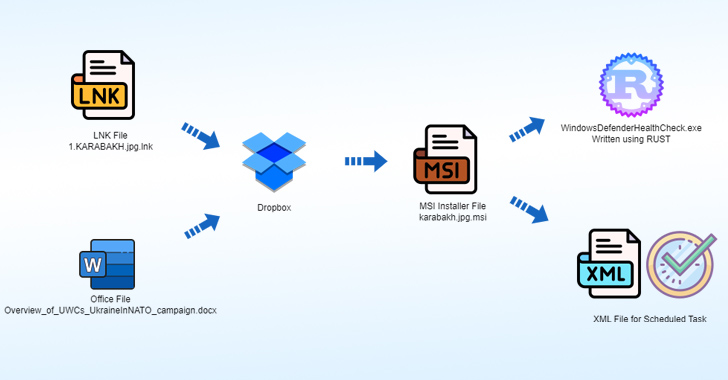
The attack chain leverages an LNK file named 1.KARABAKH.jpg.lnk as a launchpad to retrieve a second-stage payload, an MSI installer, hosted on Dropbox.
The installer file, for its part, drops an implant written in Rust, an XML file for a scheduled task to execute the implant, and a decoy image file that features…