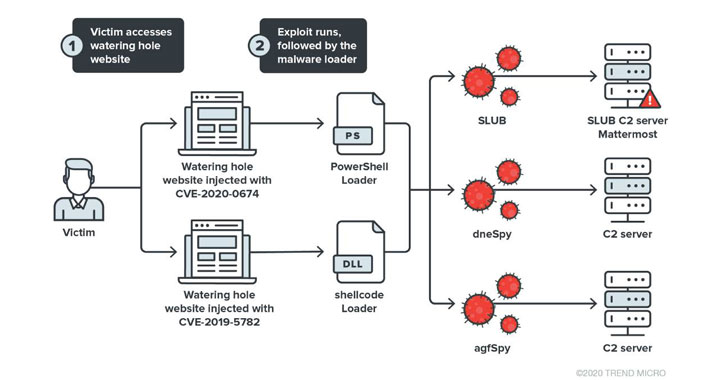
Cybersecurity researchers have disclosed details about a new watering hole attack targeting the Korean diaspora that exploits vulnerabilities in web browsers such as Google Chrome and Internet Explorer to deploy malware for espionage purposes.
Dubbed “Operation Earth Kitsune” by Trend Micro, the campaign involves the use of SLUB (for SLack and githUB) malware and two new backdoors — dneSpy and agfSpy — to exfiltrate system information and gain additional control of the compromised machine.
The attacks were observed during the months of March, May, and September, according to the cybersecurity firm.
Watering hole attacks allow a bad actor to compromise a targeted business by compromising a carefully selected website by inserting an exploit with an intention to gain access to the victim’s device and infect it with malware.
Operation Earth Kitsune is said to have deployed the…