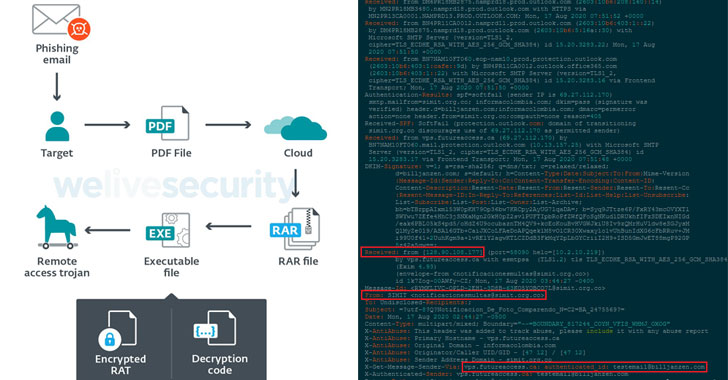
Cybersecurity researchers took the wraps off an ongoing surveillance campaign directed against Colombian government institutions and private companies in the energy and metallurgical industries.
In a report published by ESET on Tuesday, the Slovak internet security company said the attacks — dubbed “Operation Spalax” — began in 2020, with the modus operandi sharing some similarities to an APT group targeting the country since at least April 2018, but also different in other ways.
The overlaps come in the form of phishing emails, which have similar topics and pretend to come from some of the same entities that were used in a February 2019 operation disclosed by QiAnXin researchers, and subdomain names used for command-and-control (C2) servers.
However, the two campaigns diverge in the attachments used for phishing emails, the remote access trojans (RATs) deployed, and the C2 infrastructure employed to fetch the malware dropped.
The attack chain begins with the targets…