Mobile users in Brazil are the target of a new malware campaign that delivers a new Android banking trojan named Rocinante.
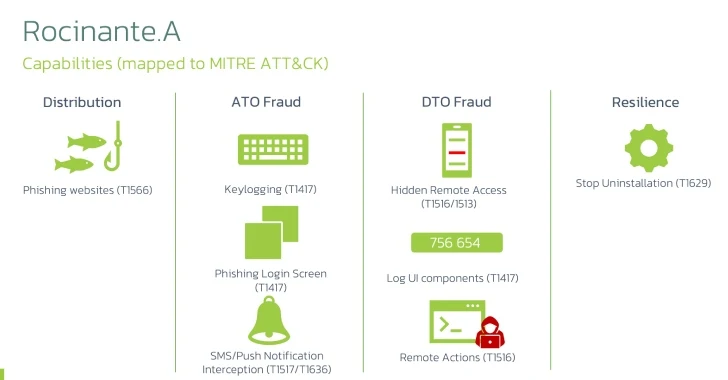
“This malware family is capable of performing keylogging using the Accessibility Service, and is also able to steal PII from its victims using phishing screens posing as different banks,” Dutch security company ThreatFabric said.
“Finally, it can use all this exfiltrated information to perform device takeover (DTO) of the device, by leveraging the accessibility service privileges to achieve full remote access on the infected device.”
Some of the prominent targets of the malware include financial institutions such as Itaú Shop, Santander, with the phony apps masquerading as Bradesco Prime and Correios Celular, among others –
- Livelo Pontos (com.resgatelivelo.cash)
- Correios Recarga (com.correiosrecarga.android)
- Bratesco Prine (com.resgatelivelo.cash)
- Módulo de Segurança (com.viberotion1414.app)
Source code analysis of the malware has revealed that…