StrongPity or Promethium APT, also referred to as APT-C-41, has been active since 2012. It had been first publicly reported in October 2016, after cyberattacks against users in Belgium and Italy during which it used the watering-hole attack technique to deliver malicious versions of WinRAR and the TrueCrypt file encryption software.
The group mainly uses Truvasys, a first-stage malware used with trojanized common computer utilities, including WinUtils, TrueCrypt, WinRAR, or SanDisk.
Distinctive features of StrongPity APT
Researchers explain that StrongPity APT employs zero-day vulnerabilities and sophisticated attack tools to invade victims for espionage.
At present, the threat actors have expanded its TTPs to include watering hole attacks and mass phishing email campaigns.
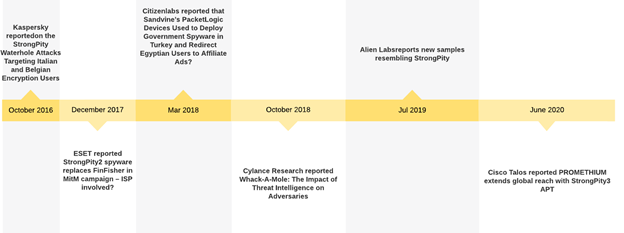
High-level process flow of the StrongPity malware
The high-level execution flow of the StrongPity infection (as shown in the image below) is as follows:
- The APT actor employing…

















