Researchers have disclosed a security shortcoming affecting three different WordPress plugins that impact over 84,000 websites and could be abused by a malicious actor to take over vulnerable sites.
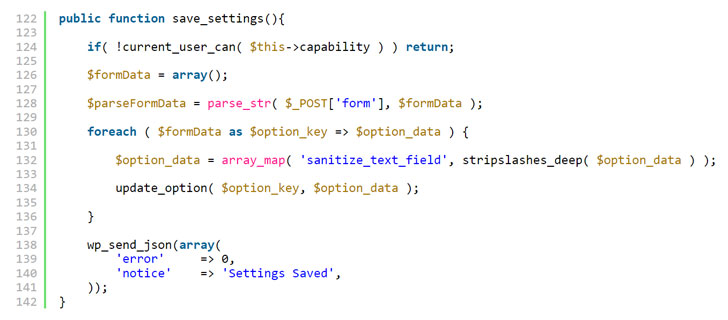
“This flaw made it possible for an attacker to update arbitrary site options on a vulnerable site, provided they could trick a site’s administrator into performing an action, such as clicking on a link,” WordPress security company Wordfence said in a report published last week.
Tracked as CVE-2022-0215, the cross-site request forgery (CSRF) flaw is rated 8.8 on the CVSS scale and impacts three plugins maintained by Xootix —
Cross-site request forgery, also known as one-click attack or session riding, occurs when an authenticated end-user is tricked by an attacker into submitting a specially crafted web request. “If the victim is an administrative account, CSRF can compromise the entire web application,” OWASP notes in its documentation.
Specifically, the vulnerability has its…